According to Microsoft Developer Network, HttpOnly & Secure is an additional flag included in the Set-Cookie HTTP response header. Using HttpOnly in Set-Cookie helps in mitigating the most common risk of an XSS attack. This can be either done within an application by developers or implementing the following in Tomcat. As a best practice, take a backup of configuration file before modifying and if the possible test in non-production to ensure it doesn’t break the application. Let’s see how to achieve this.
Implement HttpOnly & Secure flag in Tomcat 6.x
Log in to Tomcat server Go to Tomcat installation path and then conf folder Open context.xml using vi editor and update Context section as below
Ex:
Next, adding a secure flag.
Open server.xml and add below in Connector port section
Restart Tomcat server to test the application
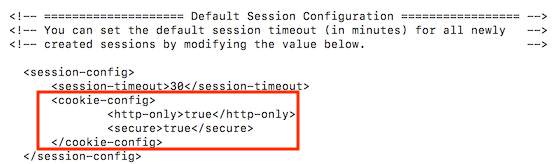
Implementing in Tomcat 7.x/8.x/9.x
Go to Tomcat » conf folder Open web.xml and add below in session-config section
Ex:
Save the file and restart Tomcat to test it.
Verification
There are multiple ways. If you are testing Intranet applications, then you can use developer tools inbuilt in the browser like Chrome, IE, or Firefox. However, if Internet-facing or want to test it externally then it can use HTTP Header Checker online tool. I hope this adds a layer of Tomcat security. Learn more about Tomcat administration here.